Firefox Local Files Theft - CVE-2019-11730

Recently, I was performing a research on Same Origin Policy attacks, I managed to realize that the la
version of Firefox (currently 67) is vulnerable to local files theft attack (on any supported OS), due to improper implementation of Same Origin Policy for file scheme URIs.
Let’s go over the PoC details then I will provide an explanation of why its not patched yet.
Attack scenario:
-
Attacker sends email to victim with attachment file to be downloaded / Victim browse to malicious website and download file
-
The victim opens the HTML malicious file
-
The file loading the containing folder in an iframe (so my file path is
file:///home/user/-malicious.html, and the iframe source will befile:///home/user/) -
The victim thinks he clicks on a button on the malicious HTML, but in fact he is clicking on the malicious file html inside the iframe’s directory listing (using ClickJacking technique, in order to apply the “context switching bug” which allows me access the directory listing of my containing folder)
-
The malicious iframe now have escalated privileges and is be able to read any file on the folder contains the malicious file, (in most cases downloads folder, in my case is
file:///home/user/). -
The malicious file is able to read any file on it’s containing folder (
file:///home/user/), such as SSH private key by simply fetching the URLfile:///home/user/.ssh/ida_rsaand stealing any file by 1 more fetch request to the attacker’s malicious website with the files’ content. -
The attacker gains all files in the folder containing the malicious file exploit this vulnerability
So let’s dig into the details, in my opinion, the core issue starts in the web origin concept RFC which is not describing a well-defined implementation of SOP for file scheme URIs.
Page 10:
If uri-scheme is "file", the implementation MAY return an implementation-defined value.
NOTE: Historically, user agents have granted content from the
file scheme a tremendous amount of privilege. However,
granting all local files such wide privileges can lead to
privilege escalation attacks. Some user agents have had
success granting local files directory-based privileges, but
this approach has not been widely adopted. Other user agents
use globally unique identifiers for each file URI, which is
the most secure option.
So basically, the RFC says “the implementation MAY return an implementation-defined value”, if I understand it right, in simple words, it says “You can do whatever you want”, which is not so make sense to me.
In addition, some approaches regarding this are presented:
- Granting local files tremendous amount of privilege - which is insecure. (Currently, no browser implemented it)
- Graning local files directory-based privileges - which is insecure, but less than the previous one (Currently, implemented only by Firefox)
- Graning local files file-based privileges - which is secure. (Currently, implemented by Chromium and Edge)
We all understand that the 1st choise is insecure, but the 2nd option is quite problematic as well, and was adopted by Firefox, and this is the exact reason how I was managed to perform the attack described at the beginning of this article.
| Vector | Firefox | Chromium | Safari | Edge | |
|---|---|---|---|---|---|
| Directory-based Same Origin Policy | V | X | X | X | X |
| Disallow fetch to file scheme | X | V | V | V | V |
As you can see, in addition to the fact dir-based SOP implementation is supoprted only on Firefox, all the modern browsers not allow fetch requests to file schemes, which is accepted by Firefox:
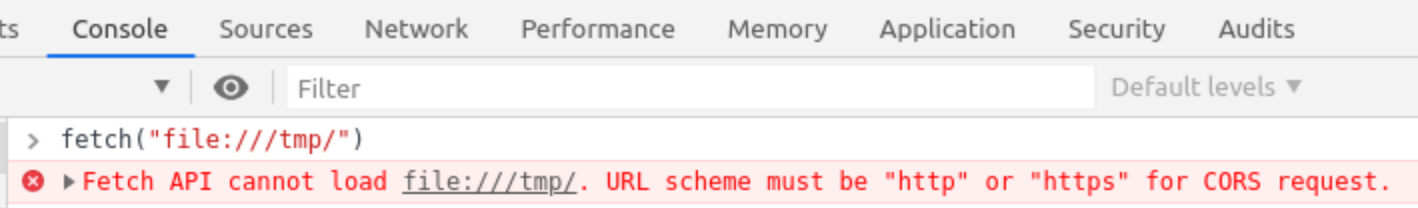
Security-wise I think this should be addressed on RFC side, that should enforce user-agents (browsers) to implement the most secure approach, and don’t allow developers do such mistakes that leaves the client be exposed to such attacks.
Although the RFC defined that SOP implementation for file schemes URIs can be insecured, Firefox adopted the insecure approach:
“Our implementation of the Same Origin Policy allows every file:// URL to get access to files in the same folder and subfolders.”
said Frederik Braun on the bug I reported few days ago, the article Same-origin policy for file: URIs explains this approch.
It is important to note, that Firefox only refers to the directory-based SOP implementation and the fact that one file can read files on in the directory, but did not refer any information regarding the fact that I was able read the entire files within the same directory, which make this attack even worse.
I was curious to see for how long Firefox ignores users complains and imeplmented this insecure approach, and it looks like forever. I was managed to get a bug reported on almost the same vulnerability (except for the directory listing context switch bug) was already reported 17 years ago :|
So looks like it is a known bug for Firefox, which chose the insecure implementation, I think this is a huge security issue that needs to be addressed ASAP, as well as the RFC shouldn’t be so permissive. I think malicious file opened in file: URI scheme shouldn’t steal the entire files list with a single click or steal a specific file path without any click.
Hopefully this article will make people aware for this vulnerability and Firefox will understand the risk and address this issue.
