Gem in a box XSS vulnerability - CVE-2017-14506
In this short blogpost I will give a short explain of XSS vulnerability i found on geminabox v0.13.5. which is a gems manager like rubygems.org so you can upload and download gems
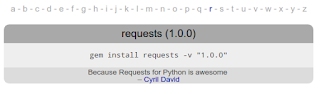
Geminabox parses the uploaded gems and gives the users list of the gems on the system as the following image:
As you can see, the system parses the gem’s details and present it on the web UI.
After few times, I succeeded to create a GEM file to exploit XSS, the attack scenario goes as follows:
-
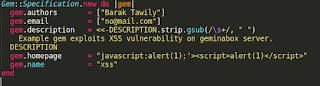
Malicious attacker create GEM file with crafted homepage value (gem.homepage in .gemspec file) includes XSS payload as the following image:
-
The attacker access geminabox system and uploads the gem file (or uses CSRF/SSRF attack to do so).
-
From now on, any user access Geminabox web server, executes the malicious XSS payload, that will delete any gems on the server, and won’t let users use the geminabox anymore. (make victim’s browser crash or redirect them to other hosts).
PoC video: https://www.youtube.com/watch?v=eFIJL7yMYFA